How it works
The software protection is composed by 2 packages :
Protect package, which must be included and linked with user application
ProtectEncrypt package, a command-line standalone app which is used by post-link custom build step to encrypt the executable after link process
The usage is quite simple and transparent to build process; to use it is enough to :
Build the ProtectEncrypt package and put its executable in some easy to locate place (system32 windows directory or /usr/bin for linux systems, for example).
You can use a 32 bit or 64 bit ProtectEncrypt build on any executable, it will detect the executable type (32 or 64 bit) and configure itself correctly.
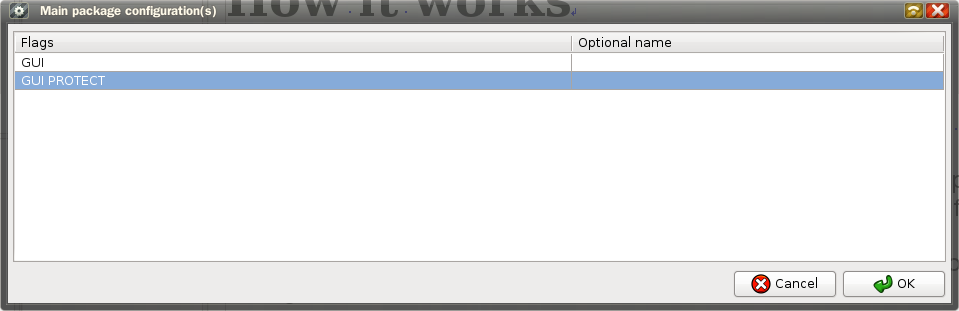
In main package configuration of application to protect, add a PROTECT flag; you can, for example, make 2 main configurations, one for testing, without protection, and another with protection for deploying purposes :
Add a post-link custom build step, which run the ProtectEncrypt code encryptor after the link phase :
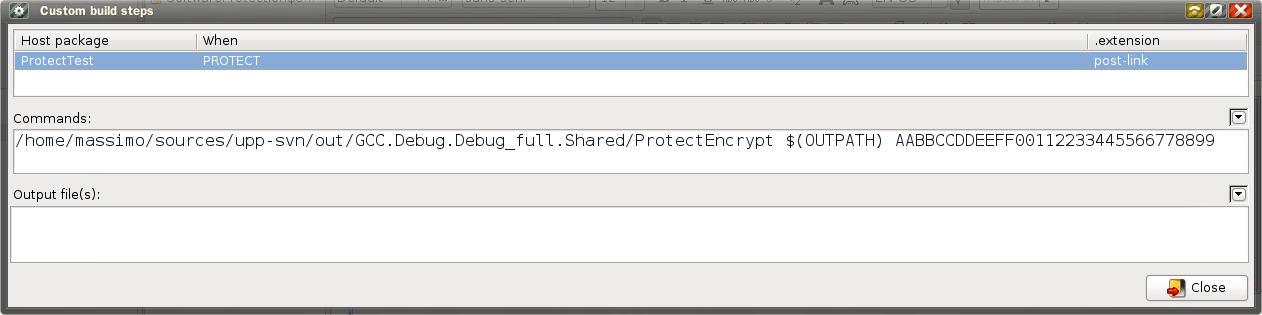
You can see the ProtectEncrypt invocation (here with full path, if you placed it on a system folder you can just use the app name); first parameter $(OUTPATH) represents the executable to be encrypted, and must not be changed; second parameter (here AABBCC...8899) is the encryption key, which MUST be 128 or 256 bits long (16 or 32 bytes), written as an hex-ascii string, every 2 chars represent 1 hex byte.
Add Protect package to your app, and include its header :
#include <Protect/Protect.h>
In your application, enclose parts of code you want to be encrypted by mean of PROTECT_START_FUNC(GetCypher) and PROTECT_END_FUNC macros :
void MyEncryptedFunction(void)
{
PROTECT_START_FUNC(GetCypher);
<here my function code>
PROTECT_END_FUNC;
}
Former limitation of not being able to encrypt code containing linker fixed references (i.e.: far calls, far data access) is gone now.
Define a function (GetCypher in this case) which returns an One<Cypher> object that is uset to decrypt the code; see Cypher package for detail.
By now ProtectEncrypt use SNOW2 encryption, so you should return a SNOW2 Cypher object. This can be changed to use another encoder by modifying the ProtectEncrypt application. Here an example with an hard-coded key:
One<Cypher>GetCypher(byte const *nonce, size_t nonceLen)
{
String key = "\xAA\xBB\xCC\xDD\xEE\xFF";
return new Snow2((uint8_t const *)~key, key.GetCount(), nonce, nonceLen);
}
In a real app, the key can be read from a dongle, from a license file, from internet or generated by a combination of machine identification number and a license key.
You can also check for key correctness on app startup, and abort the app if key is incorrect; the macro ON_PROTECT_BAD_KEY(GetCypher) executes a block of code only if the key isn't correct. Here an example usage :
ON_PROTECT_BAD_KEY(GetCypher)
{
PromptOK("License error");
exit(1);
}
That's all ! If you build your application with TheIde, selecting the GUI PROTECT main configuration, it'll be automatically built and encrypted with the key you've chosen.
You can see all that working in ProtectTest demo application; if you change the key in its GetCypher() function your app will signal the license error upon run, giving the user the choice of exiting the app or continue anyways. Of course, if you choose to continue, the app will crash.
If the key is correct, no alert is shown and the app runs normally.
The code is smart enough to work around at code optimizations, and it should work both on 32 and 64 bit compilers; it doesn't use any inline assembly, so it is usable also on 64 bit MSC.
On next chapter we'll introduce another kind of copy protection tool named obfuscation.
|
